Preface
What is money laundering?
Money laundering is a complex and illegal process through which individuals or organizations attempt to conceal the origins of illegally obtained money, making it appear as if it comes from legitimate sources. The primary goal of money laundering is to "clean" the so-called "dirty money" so that it can be freely used without raising suspicion.
Why use crypto currency as a way to do money landering?
During the early days of cryptocurrency, there were relatively fewer regulations and established systems in place to manage its use. This lack of oversight, combined with the inherent features of cryptocurrencies such as anonymity, pseudonymity, and the absence of central authorities, created an environment in which criminals could more easily hide their identities and engage in illegal activities. Also it's easier to transfer the asset out of the country they stay, in this case it's harder for investigators to track the money.
Nowadays
As cryptocurrencies gained popularity and attention, regulatory efforts increased to address these concerns. Governments and financial authorities around the world began developing and implementing measures to regulate the cryptocurrency space, including:
- Know Your Customer (KYC) and Anti-Money Laundering (AML) Regulations
- Licensing and Registration for cryptocurrency businesses
- Taxation
- Blockchain Analysis
Today, we will introduce some common behavioral patterns that serve as red flags in cryptocurrency trading.
Multiple Transfers
- Making multiple small amounts of transactions
According to regulations, large and irregular transactions can attract the attention of government or financial authorities. All legitimate financial institutions that require their customers to undergo Know Your Customer (KYC) procedures are obligated to report such transactions. This heightened scrutiny exposes criminal activities to authorities.
That's why one of the reason why criminals would do multiple trasnfers is to structure transactions in small amounts that are under record-keeping or repoerting threshold. It's also a common pattern in cash money laundering.
- Making multiple high-value amounts of transactions
By spacing out the transactions and making them appear regular, criminals may attempt to make the transactions seem more like legitimate trading or investment activity. This can further mask the illicit nature of the funds and decrease suspicion.
- Making multiple transactions to multiple virtual assets service providers.
Criminals often try to transfer their assets to virtual asset service providers located in somewhere that is no relation to where the customer lives or conducts business; or jurisdictions with either weak or no Anti-Money Laundering/Counter-Financing of Terrorism (AML/CFT) regulations. This strategy complicates investigators' efforts to trace the origin of the funds and resources.
Multiple Receives
Making frequent transfers to the same virtual asset (VA) account within a specific period of time, especially when it involves multiple individuals, transactions from the same IP address, or significant amounts, can raise red flags for several reasons:
Criminals often use a single address to aggregate funds obtained from various sources, including illegal activities such as scams, theft, or ransomware. Multiple receives into a single address can indicate the consolidation of these illicit funds.
Structuring, also known as smurfing, involves breaking down large sums of money into smaller transactions to avoid triggering reporting thresholds and attracting regulatory attention.
In some cases, middlemen or intermediaries may be involved in cryptocurrency transactions. These middlemen may use multiple receives to distribute funds or to anonymize the transaction. This can make it difficult to identify the ultimate sender or receiver.
Multiple Deposits
This typically occurs with individuals or organizations that possess multiple virtual asset addresses. They break down their illicitly obtained funds into smaller amounts, deposit them to one or multiple exchanges or virtual asset service providers then converting them into various cryptocurrencies. This process incurs additional transaction fees,but without logical business explanation. Or after depositing, they withdrawing virtual assets (VAs) from a virtual asset service provider (VASP) and promptly transferring them to a private wallet effectively transforms the exchange or VASP into a money laundering mixer. It usually happens without additional exchange or investment activity, which is an unnecessary step and incurs transaction fees.
Multiple Withdraws
Criminals involved in money laundering may withdraw funds in multiple small transactions to avoid detection. This technique, known as "structuring" or "smurfing," is used to break down large sums of money into smaller, less conspicuous withdrawals to circumvent reporting thresholds.
In some cases, identity thieves may make multiple withdrawals from a victim's account as part of their fraudulent activities.
With Black List
Addresses linked to criminal activities, such as hacking, fraud, theft, or other unlawful actions, will be placed on BAIFA's Black List. Accepting funds from addresses on the Black List is considered to be aiding money laundering.
OFAC-Specially Designated Nationals and Blocked Persons List
With Darknet (Darkweb)
The darknet itself is not inherently illegal. It's a part of the internet that is intentionally hidden and not indexed by traditional search engines. It can provide a level of privacy and anonymity for users. It's used by journalists, activists, whistleblowers, and individuals living in countries with strict censorship to communicate and share information without fear of surveillance or censorship.
Meanwhile, Darknet markets, also known as underground or hidden markets, are online platforms that operate on the dark web and are accessible through specialized software. These markets facilitate the buying and selling of a wide range of illegal goods and services, including drugs, stolen data, counterfeit documents, hacking tools, and more. Criminals use these markets to conduct illicit transactions.
Many darknet markets primarily use cryptocurrencies like Bitcoin for transactions. Cryptocurrencies provide a degree of anonymity, making them an attractive choice for conducting illegal activities. Criminals often use cryptocurrencies to pay for illegal goods and services on darknet markets.
With Mixing Service
Mixing and tumbling services are methods used in the world of cryptocurrency to enhance the privacy and anonymity of transactions. These services aim to obscure the source and destination of funds, making it difficult to trace the flow of cryptocurrency.
Mixing Services (Coin Mixing or CoinJoin):
- Multiple users send their cryptocurrency to a mixing service.
- The mixing service combines these funds into a pool.
- It then redistributes the cryptocurrency to the intended recipients, but in a way that makes it challenging to associate specific inputs with specific outputs. This process breaks the transaction history, enhancing privacy.
Tumbling Services (Bitcoin Tumblers or Tumblers):
Tumbling services work similarly to mixing services but with a focus on Bitcoin. They aim to "tumble" or "shuffle" Bitcoins to break the transaction history. Here's how it works:
- Users send their Bitcoins to a tumbler service.
- The tumbler service mixes these Bitcoins with other users' coins.
- The service then sends the mixed Bitcoins back to the users, but in randomized amounts and at different times.
- As a result, it becomes challenging to link the original Bitcoins to their source.
With Gambling Site
Another method commonly employed for cryptocurrency money laundering involves online gambling. With the increasing acceptance of cryptocurrencies on various online gambling and gaming websites, criminals have found a seemingly simple way to legitimize their illicit funds. Here's how it works:
- Access to Online Gambling Sites: Criminals access online casinos, sports betting platforms, or other gaming websites that accept cryptocurrencies as a means of payment.
- Purchasing Credits: They use their cryptocurrency to purchase in-game credits, virtual chips, or tokens on these platforms.
- Gameplay: To create a façade of legitimacy, the money launderers engage in actual gameplay, making bets and playing rounds of games.
- Cashing Out: After a few rounds or bets, they cash out their cryptocurrency, often in multiple small transactions.
- Legitimization: By doing so, they provide themselves with a plausible explanation for the source of the funds. They can assert that their winnings in these online games account for the money cashed out.
It's important to recognize that money launderers are not motivated by the desire to profit from gambling; rather, they seek to legitimize their ill-gotten gains and avoid suspicion.
Large Transfer (High-value Transfer)
Risk of Money Laundering: To save the time,high-value transactions can be used by criminals as a means to legitimize illicit funds. Money launderers may seek to move significant sums of money through legitimate channels to obscure the source of their illegal gains.
Potential for Terrorist Financing: High-value transactions can also be indicative of terrorist financing, where individuals or organizations attempt to move substantial funds to support illegal activities or terrorist operations.
Scam or fraud: High-value transfers may be connected to investment scams or fraudulent schemes where victims are convinced to transfer substantial sums of money, often with the promise of significant returns.
Hacking: Hackers may target financial institutions, exchanges, or payment processors, gaining access to their systems. This access can enable them to initiate high-value transfers directly from these institutions.
When investigating the potential link between a high-value transfer and illegal activity, investigators carefully evaluate factors like the source of funds, transaction history, purpose of the transfer, and relationships involved. This is why the "Know Your Customer" (KYC) process is a crucial step for financial institutions. KYC helps identify irregular transactions and discrepancies between the transaction amount and the client's background, enabling institutions to report and address suspicious activities effectively.
Large Receipt (High-value Receipt)
High-value receipts and high-value transfers share the same concept but involve different roles for senders and recipients.
Large Deposit (High-value Deposit)
Money Laundering: Criminals involved in illegal activities often need to legitimize their ill-gotten gains. Making a large deposit is one way they may attempt to introduce significant sums of money into the legitimate financial system.
Layering: Money launderers may engage in a technique called "layering," which involves multiple transactions to obscure the source of funds. Large deposits can be one part of this process as they may be followed by other transactions aimed at further disguising the origin of the money.
Unusual Activity: Deposits into an account or a VA address are significantly higher than ordinary with an unknown source of funds, followed by conversion to fiat currency, which may indicate theft of funds.
Large Withdraw (High-value Withdraw)
Money Laundering: Suspicion arises, particularly when engaging in VA-fiat or VA-VA currency exchanges with the potential for financial losses. This could indicate attempts by criminals to convert and withdraw their illicit funds, possibly after undergoing multiple money laundering processes or utilizing Virtual Asset Service Providers as mixers before transferring the assets to another address.
Hacking: Hacking enables unauthorized access to financial systems, accounts, or crypto wallets, leading to large amount withdrawals. This may stem from stolen credentials, ransomware, phishing, account takeovers, and insider threats.
To High Risk Location
When customers send funds to unregulated or inadequately regulated Virtual Asset Service Providers (VASPs), it can raise suspicions, particularly when the customer's location does not align with the jurisdiction of the VASPs involved. This heightened risk is associated with concerns related to illicit activities, money laundering, and attempts to evade Anti-Money Laundering and Countering the Financing of Terrorism (AML/CFT) controls.
Black List on FATF (Updated in June, 2023)
The "Black List" identifies countries or jurisdictions with significant deficiencies in combating money laundering, terrorist financing, and proliferation financing. These nations are urged to take counter-measures to safeguard the international financial system from the risks associated with these illicit activities.
- North Korea
- Iran
- Myanmar
Grey List on FATF (Updated in June, 2023)
The "Grey List" highlights countries collaborating with FATF to address money laundering, terrorist financing, and proliferation financing issues. Increased monitoring signifies their commitment to swiftly resolve these deficiencies within agreed timeframes.
- Albania
- Barbados
- Burkina Faso
- Cameroon
- Cayman Islands
- Croatia
- Democratic Republic of Congo
- Gibraltar
- Haiti
- Jamaica
- Jordan
- Mali
- Mozambique
- Nigeria
- Panama
- Philippines
- Senegal
- South Africa
- South Sudan
- Syria
- Tanzania
- Türkiye
- Uganda
- United Arab Emirates
- Vietnam
- Yemen
Transactions with Privacy Coins
Privacy coins like Monero, Zcash, or Dash are designed to provide enhanced privacy and anonymity. While this feature can protect users' identities, it also makes it challenging for authorities and financial institutions to trace and monitor transactions. This lack of transparency can trigger concerns, as it may hinder the detection of illicit activities such as money laundering, tax evasion, and the financing of criminal enterprises.
How Privacy Coins work
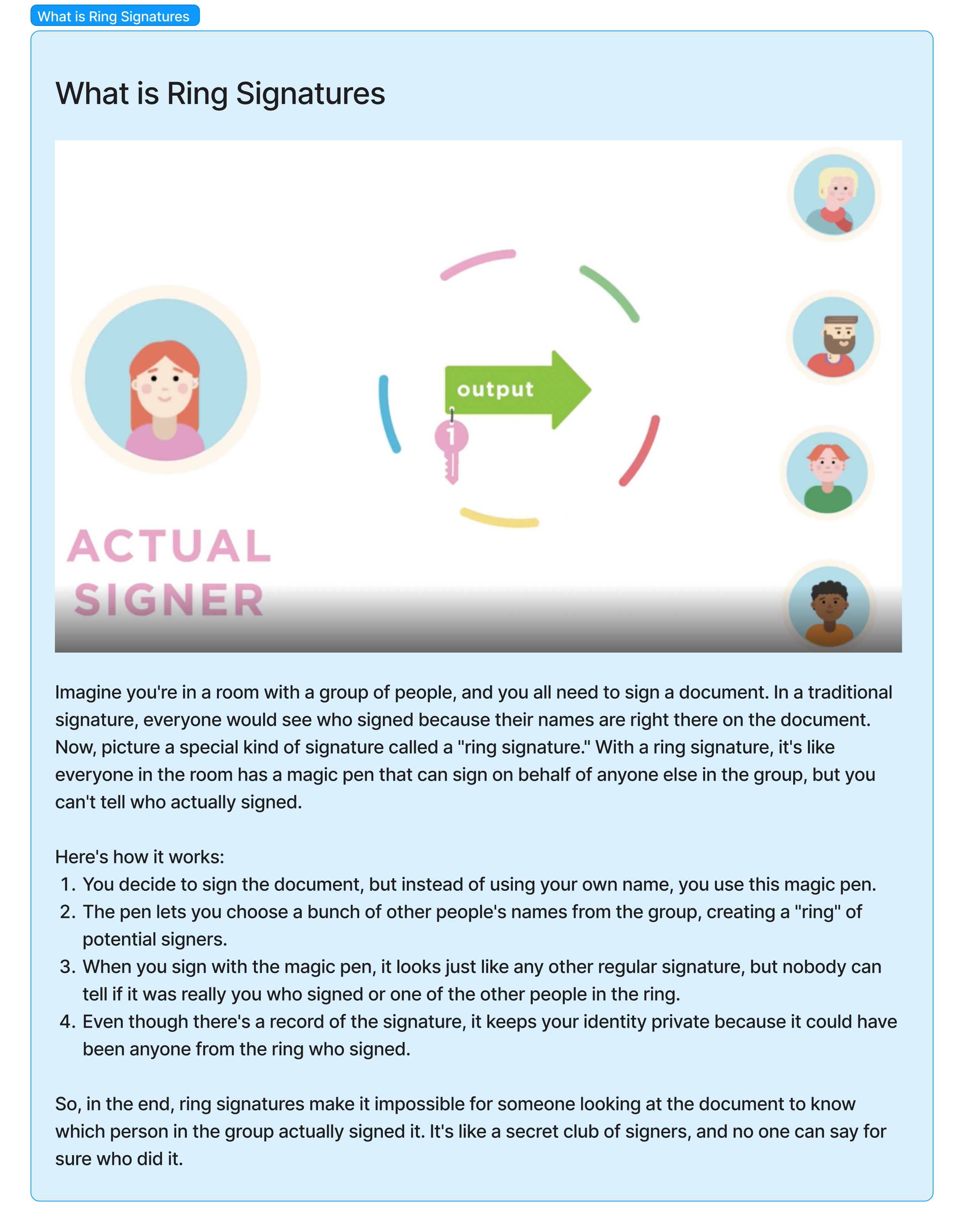
- Ring Signatures (Monero) 環狀簽名: In Monero, for example, when a user initiates a transaction, their transaction is mixed or "ringed" with several other transactions on the network. This makes it challenging to determine which specific input (or source) corresponds to the actual sender's funds.
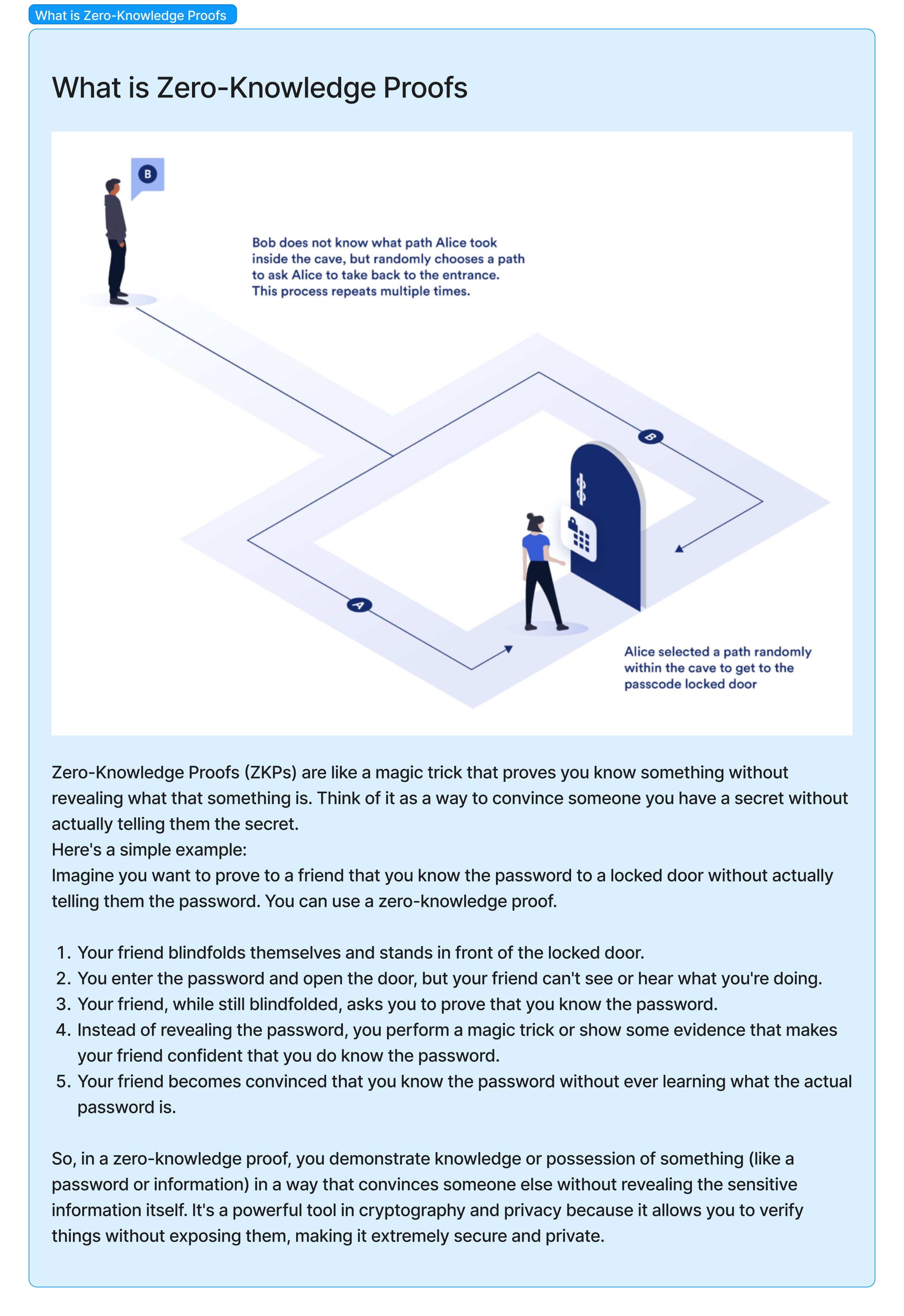
- Zero-Knowledge Proofs (Zcash) 零知識證明: In Zcash, zero-knowledge proofs enable the network to verify that a transaction is valid without revealing the sender's address, receiver's address, or transaction amount. The mathematical proof demonstrates that a transaction meets the network's rules without revealing any sensitive information.
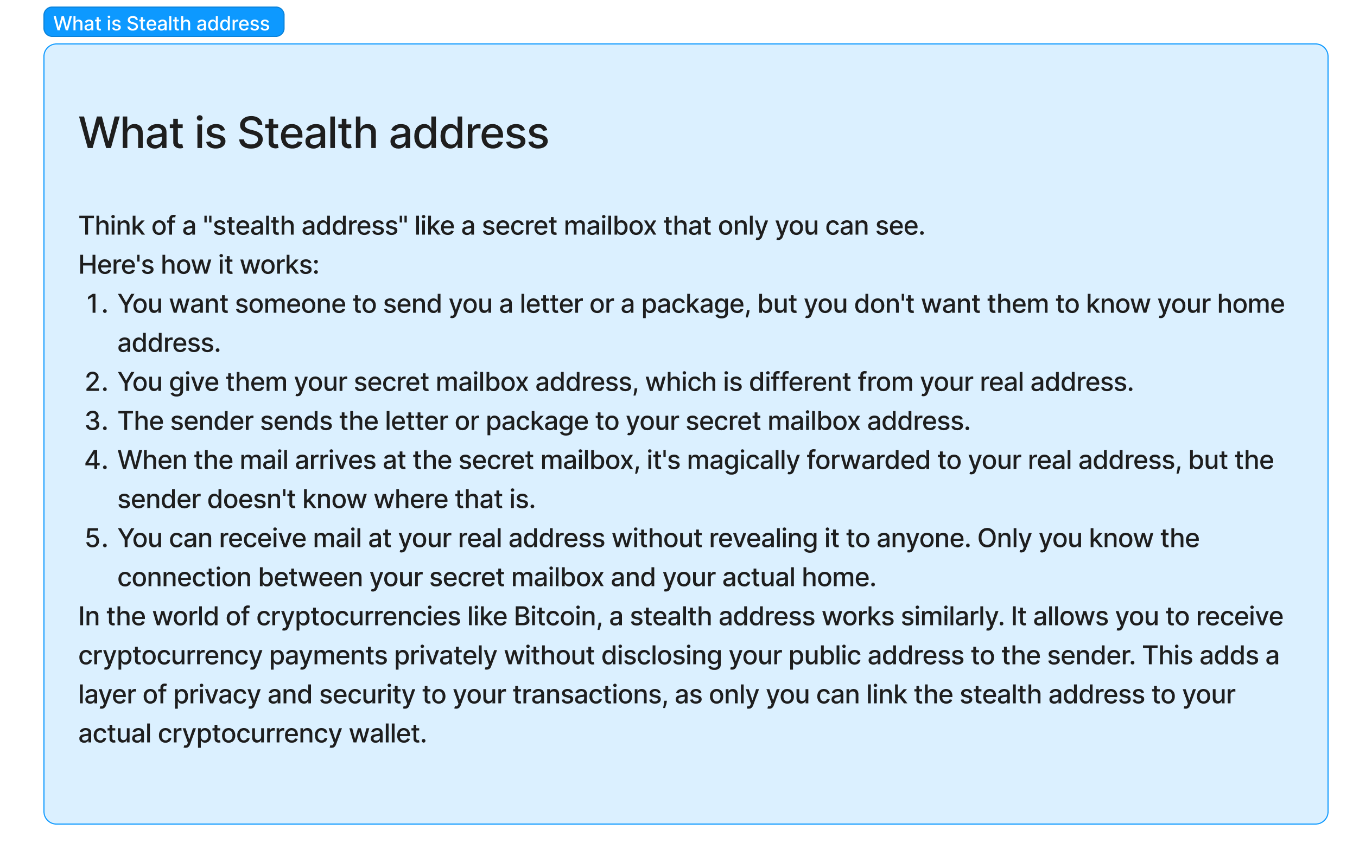
- Stealth Addresses 隱身地址: Privacy coins often use stealth addresses to provide recipients with a unique, one-time public address for each transaction. This means that even if someone knows your public address, they cannot link it to specific transactions because each transaction uses a different stealth address.
Confidential Transactions 保密交易: Some privacy coins, like Grin or Beam, implement confidential transactions. These cryptographic techniques encrypt the transaction amount, making it challenging for outsiders to determine the exact value being transferred.
CoinJoin (Optional): Some privacy coins offer optional CoinJoin functionality, which allows multiple users to pool their transactions into a single transaction, making it difficult to trace individual transactions within the mix.